When we start working on a new project, many times we add third party dependencies for some common functionalities. These libraries themselves are also dependent on another set of dependencies to provide the functionality in the same package. Although it is not an issue to use dependencies, but over time there are a lot of them. So, it becomes necessary to find out which one of these has any vulnerabilities.
In general, the more dependencies your project uses, the more complex your dependency tree will be and hence the risk of vulnerability. You can use static code analysers to find out if there are any bugs introduced in your code, but what about third-party dependencies? This is where dependency vulnerability checker comes in handy.
OWASP Dependency checker to find vulnerabilities in java projects
OWASP dependency checker is an open-source software that checks your project dependencies for known publicly disclosed vulnerabilities. It will inspect dependencies used by your application/ project and collect evidence from the Common Platform Enumeration (CPE) for each of these. If there are evidences found for a particular library, listing associated with the corresponding library in CVE are listed in the report.
The dependency checker is available as:
- Ant Task.
- Command Line tool.
- Gradle plugin.
- Jenkins plugin.
- Maven plugin (For maven version 3.1 or higher).
- SBT plugin.
OWASP IDE Integration?
As mentioned earlier, there is no official support for IDE. Instead, it is straightforward to integrate it in your build process.
OWASP Maven plugin
The maven plugin is pretty straight forward to use. All you must do is add the maven dependency and the plugin goal. The latest version of the plugin (as of writing this article) is 6.1.6, which can be downloaded from here. Just add the following plugin to your pom:
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId
<version>6.1.6</version>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>And run the command from your project directory:
mvn clean verifyIt will start downloading the required dependencies to find the vulnerabilities.
Please do note that when you run the above command for the first time, then it may take up to 20 minutes to complete since it downloads and processes all the data from the National Vulnerabilities Database, i.e., NVD. After the initial download, the subsequent checks should not check more than a couple of seconds to run if you run it at least once every 7 days.
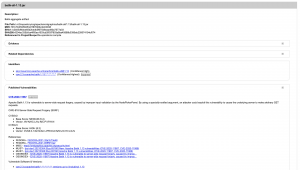
Once the above command has been executed successfully, it should generate an html file in the target folder of your maven project. This file will have the list of all affected dependencies. For each of these affected libraries, you will even find that there are a lot of other important details like Highest Severity level, the CPE confidence along with the CVE count.
Clicking on individual dependency will also show the details of the vulnerability. For instance, see the following screenshot for the batik-all-1.13.jar file:
Or if you prefer to generate the report in clean CSV format, you can run the following command:
mvn clean verify -Dformat=CSVThis CSV file will include all the details about the vulnerabilities present in the HTML file in neat tabular format which is useful for documentation rather than HTML.
Generating aggregated dependency check reports
If you have a project with multiple modules, then you can generate an aggregated report by using the following config in your pom:
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>6.1.6</version>
<reportSets>
<reportSet>
<reports>
<report>aggregate</report>
</reports>
</reportSet>
</reportSets>
</plugin>From the terminal, run the following command to generate HTML reports
mvn org.owasp:dependency-check-maven:aggregateAnd for CSV reports, just add the flag
mvn org.owasp:dependency-check-maven:aggregate -Dformat=CSVFailing build based on CVS score
As I had mentioned earlier, there are scores assigned to every vulnerability. So, what if you wanted to set a threshold score, let’s say of 5, and want the build to fail if the score is greater than equal to 5? To do that, just use the following configuration in your plugin block:
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>6.1.6</version>
<configuration>
<failBuildOnCVSS>5</failBuildOnCVSS>
</configuration>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>And the run the following command from the project directory:
mvn clean verifySkip checking artifacts that are not part of the final build.
There are certain dependencies that are not present in the final build. For instance, if you add libraries with test/provided scope, they are not present in the final package. So, in such scenarios it makes sense to skip checking these libraries for vulnerabilities. To do so, just add the following configuration to the plugin section of your pom:
<plugin>
<groupId>org.owasp</groupId>
<artifactId>dependency-check-maven</artifactId>
<version>6.1.6</version>
<configuration>
<skipProvidedScope>true</skipProvidedScope>
<skipRuntimeScope>true</skipRuntimeScope>
</configuration>
<executions>
<execution>
<goals>
<goal>check</goal>
</goals>
</execution>
</executions>
</plugin>2. OWASP command line tool
The command line tool comes in handy if you want to scan your repository. It can be installed on MacOS using brew
brew install dependency-checkIn order to find vulnerabilities, run it using the following command:
dependency-check --project Dependency-Check-Demo --out . --scan ~/demoThe -out flag is used to specify the location to save the output HTML file.
For Windows and Linux, you can download the latest release from the Github release page here.
To scan a folder on your system, you can run the following on
Windows:
dependency-check.bat --project Dependency-Check-Demo –scan "C:\Documents\java\lib"Linux:
dependency-check.sh --project Dependency-Check-Demo --scan ~/java/libTo view all the command line arguments, you can run the following command:
Windows:
dependency-check.bat –helpLinux:
dependency-check.sh –helpFor more command line options, you can check out this link: https://jeremylong.github.io/DependencyCheck/dependency-check-cli/arguments.html
OWASP Dependency Check plugin for Jenkins
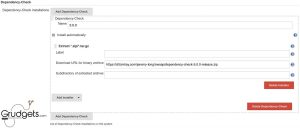
This is a handy plugin that can be integrated with your CI pipeline. Integrating is pretty straightforward, just install the plugin from Jenkins marketplace and head over to the global tool configuration page, in case changes are required. Once installed, it will display the following options in the project configuration page.
Just select the argument and it is done. Once the next build is triggered, then it will start showing the vulnerabilities present in your build/ package on the dashboard itself. You can refer the screenshot below for more details.

Final words
The OWASP dependency checker is an awesome plugin to either integrate with your CI builds or use locally. It will be useful if you are planning to use open source projects which might have outdated library versions. On the other hand, it will be useful for your own projects as well to keep out from using old or vulnerable libraries.


![Wondershare MobileGo for Android review [Windows version]](https://grudgets.com/wp-content/uploads/2014/06/App-manager-150x150.jpg)





Leave a Reply